What is a Zero Day Exploit? (and Backdoors)
You may have heard people talking about them, as I sometimes do, but what are they?
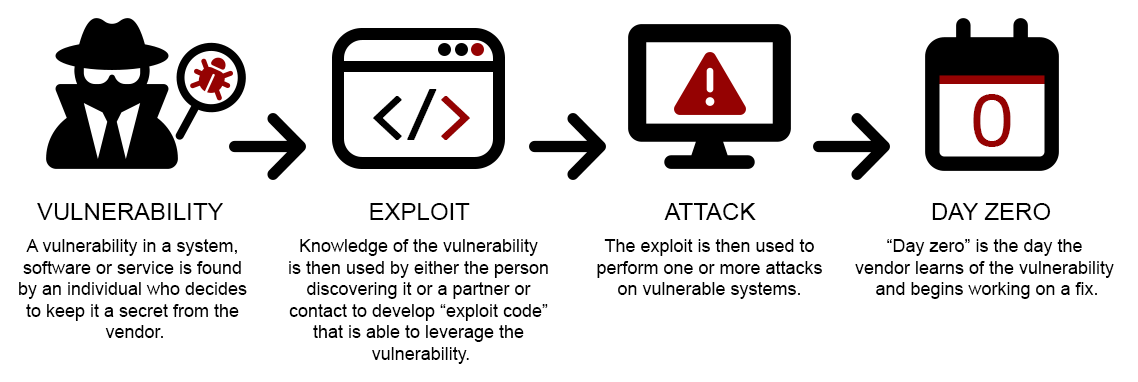
In simple terms, a zero‑day (0‑day) exploit is a vulnerability in software, hardware, a protocol or similar that is unknown to both the vendor and the public at the time it’s discovered.
Because the vendor is unaware of the problem they have zero days in which to develop, test, and release a patch… meaning the vulnerability can immediately be exploited by attackers (i.e. weaponised) with little or no resistance.
Because I’m not an artist, I’ve “borrowed” this image from the internet. And to give full credit to the author, I’ve linked it to the page I got it from.
Zero-day vulnerabilities are worth money, both to the good guys and the bad.
The good guys (ethical hackers and bug bounty researchers) will discover a vulnerability and notify the vendor through one of a number of channels. The vendor will then usually pay (through a “bug bounty” program) the discoverer and prioritise developing and testing a fix. Once that patch fix is released (which could take anywhere from a couple of weeks to a few months) the vulnerability is publicly disclosed (usually in the release note if nowhere else) and all users of the software are encouraged to update to the latest release level to keep their system secure. Obviously any unpatched systems are now even more vulnerable to hacking, because the vulnerability has been publicised to all criminals, which is why it’s important to keep your software up to date.
The bad guys (criminals and nation states) will discover a vulnerability and either seek to immediately exploit the vulnerability themselves, or sell the information (often on the dark web and other underground markets) where other criminals and nation states will pay the discoverer for the information in order to develop their own exploits. Depending upon the exact nature of the vulnerability, and who buys the knowledge, the discoverer can sometimes receive in excess of a million dollars for their work. Nation‑states will usually pay more than criminal gangs because they can use the vulnerabilities for intelligence‑gathering or sabotage, by infiltrating target networks without detection.
It should thus be obvious that, where zero day exploits are concerned, it’s a race between the good guys and the bad guys! And we should all be hoping that the good guys win.
Backdoor Access
And now you know what a zero day exploit is, consider the requests that some more authoritarian and oppressive regimes occasionally make of big tech to provide “backdoor access” to their platforms, for surveillance purposes. And what that could potentially lead to.
A recent example would be UK Government’s secret “request” to Apple to breach user privacy globally to facilitate its desire to better spy on ordinary citizens:
Apple pulls data protection tool after UK government security row
On this occasion even the UK courts disagreed with the UK government’s desire to keep things secret:
Apple's encryption row with UK should not be secret, court rules
Reportedly, similar demands were also made of Meta, Signal etc., meaning that the UK government made an attempt to end online communications privacy entirely, in a manner even more oppressive than the Online “Safety” Act 2023. However, unlike Apple, these other vendors seemingly either lacked the desire, or resources, to go up against the UK government with a legal challenge.
And then consider the huge threat to YOUR privacy and security if that backdoor had been provided, a hacker learned of it, and successfully opened it. Because the backdoor that the UK government demanded of providers of encrypted communications technology is effectively a zero-day vulnerability just waiting to be found and exploited!
Thankfully it seems that America saved the British on this occasion, as explained here:
Or have they?
UK Still Demanding Global Access to iCloud User Data, Filings Suggest
Either way, and I know that Apple agrees with me here, the principle remains:
Any backdoor into any platform is a zero day vulnerability
just waiting to be found and exploited!
And that’s the really big takeaway here, and why we must all resist any attempt at introducing backdoors into software, hardware, or anything else to protect our privacy. And that includes IoT devices like fridges and smart-meters that automatically connect to 5G, without needing access to your Wi-Fi, meaning you can’t prevent them!