Pegasus and the Zero-Click Exploit
A single SMS or other message received by your phone can grant an attacker access to your device, without you even reading it, and no need to click anything
A while back I mentioned how the UK Government is harvesting citizens’ mobile phone numbers, by forcing people to hand them over as a necessary part of using any and every government website, in the name of Two Factor Authentication (2FA) to keep citizens safe. I described my experience with the Passport Office in this article:
UK Passport Office Data Harvesting
I recently had cause to use the UK Government Passport Office website to renew a passport. It’s a pretty slick website (other than the need to complete everything in one go, because there’s no ability to save a part-completed application and return) and the passport was printed and posted out quickly too. And thanks to the Royal Mail it even dropped thr…
A few months later I received an SMS from the Government, a different department as I was paying taxes at the time. I have yet to open and read that SMS, specifically because it was unique in its architecture, as I shall explain.
I dislike doing anything that I don’t need to on my smartphone, not least because I don’t like using the small touchscreen when I have several much larger monitors, a keyboard and a mouse on my desk. On the basis that all SMS I receive are compromised anyway (they’re unencrypted plain text delivered to a device with an operating system written by Google, and managed thereon by a Messages app provided by Google) I therefore have a Chrome browser (safely sandboxed in an isolated local instance) on my desktop device running Google’s https://messages.google.com/ service which I use to read and reply to SMS messages.
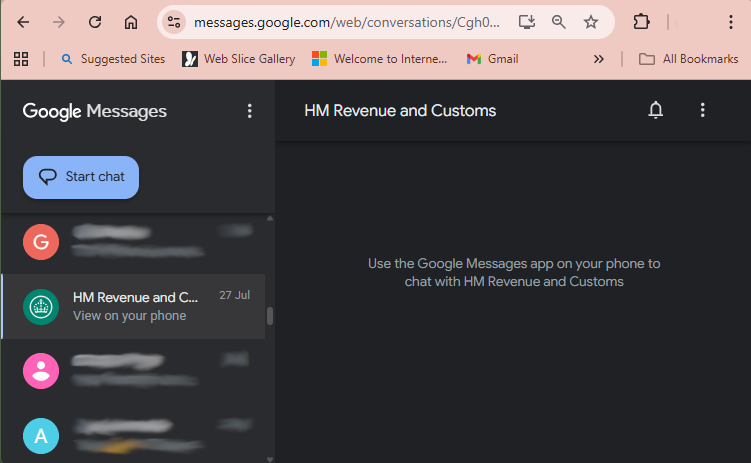
For the first time ever I was unable to read the SMS from the Government via that Google Messages Web Service running in Chrome. There was and still is no problem with SMS messages from other sources, received both before and after, just this single message from this single source as this image shows.
But looking at it in my list of unopened SMS on my smartphone there was nothing to suggest that it was in any way different. I could even see a preview, just like for any other message in the list.
It was clear that the sender of the SMS really, really wanted me to read it on my phone, not my desktop, which got me wondering why. Did that SMS perhaps contain a payload that could be executed on my smartphone, but not on my desktop? And if not, why was it configured such that I could only open it on my smartphone?
I decided to leave it unread until I understood why. And then I forgot about it.
By chance, whilst recently looking at something else for somebody else, I stumbled on a piece of “software” (that’s a polite and dignifying term for spyware produced by the Israeli company NSO Group) that can self install on most smartphones by means of what is called a zero-click exploit.
If you want to know more about NSO Group, then for a small flavour…
Politico: Israeli spyware giant NSO Group ordered to pay nearly $170M to WhatsApp for hacking accounts
Wired: Notorious Spyware Maker NSO Group Is Quietly Plotting a Comeback
BBC News: NSO Group: Israeli spyware company added to US trade blacklist
Times of Israel: NSO Group affair is latest in Israel’s long history of arming shady regimes
…but I digress. Back to the story…
For those unfamiliar with the term zero-click exploit, most exploits require that you do something, such as click a link in an email, a fake captcha, or an image (often a thumbnail on a p*rn site), before anything happens to your device. That’s a single click exploit, and it probably won’t surprise you to learn that many governments and data brokers have contracts with p*rn*graphy companies worldwide, to install their spyware on the computer of anybody that does this (it’s part of how the p*rn companies make their money, and yes it can then potentially access your webcam and microphone). But it could also land on your device through SMS, MMS, iMessage, WhatsApp, an email preview, Bluetooth, Wi-Fi, NFC or even a push notification! If you think only criminals do this you could be right, you just need to reconsider how you define criminal.
A zero-click exploit (also called a zero-interaction exploit) is what happens when their spyware is installed on your device without you doing anything at all, often exploiting a vulnerability of which the software vendor was unaware (i.e. not the conscious “back door” that certain authoritarian regimes have recently been asking for). And in the case of Pegasus there’s a lot it can do afterwards as it basically has full control of your smartphone. It’s also pretty much untraceable (as yet no anti-virus software can find it) and is designed to self-destruct (like the old Mission Impossible tapes): on command; when its job is done; if it thinks it’s likely to be detected; or if it can’t report back to base for 60 days.
Thank you NSO Group for your contribution to humanity. Although to be fair it’s perhaps only marginally worse than the Client Side Scanning which the EU would like to force on everybody and that Microsoft has already tried with Recall…
…and which I’ll cover another time, especially as Recall is back. But I digress.
If you want to learn more about Pegasus then I recommend this article by CyberNews: What is Pegasus spyware, and how can I avoid it? although, spoiler alert, you probably can’t.
Do I think that HMG/HMRC was trying to install Pegasus on my smartphone with their SMS? Honestly, I think it’s highly unlikely because I’m not a sufficiently high profile target for them, and the licensing cost of Pegasus is high.
But that’s not to say it couldn’t have been an attempt to install another similar piece of spyware, perhaps developed “in house” by the clever folk in GCHQ. I’ve not yet opened the SMS on my smartphone just in case, and I’d prefer not to because I’m sure that GCHQ’s hackers are world-class, maybe better than NSO Group’s, and unlike NSO GCHQ don’t give advance warning by marketing and selling their products either!
Why Me? Really? Am I Mad?
I may of course be barking up the wrong tree completely, and it could all be completely innocent. On the other hand, I may be onto something. I honestly don’t know. I can only guess, because deep-state activities are shadowy at best.
But IF (and that’s a big IF) UK Government are interested enough in me to try and install sophisticated spyware on my smartphone then:
I’m not going to go out of my way to make it easy for them; and
I’m sure they’ll manage somehow anyway!
Because my own personal risk assessment and technology threat assessment does not extend to considering our government a threat that I am designing my IT to mitigate against, I merely prefer to keep private from data harvesters and data brokers (of which there are thousands, as the likes of DeleteMe and Incogni will attest).
It is however interesting to consider that any government - and at this point think deep-state, because most politicians don’t have the technical knowledge to even understand the discussion let alone contribute to it, but note that Tony Blair who is notoriously anti-privacy is allegedly driving Keir Starmer from behind the scenes with his push for digital ID - that has openly expressed a desire to have more access to people’s identities, messages etc. (seemingly worldwide, not just UK) may have developed spyware to do this.
Indeed, given how clever the folks in GCHQ are I’d be extraordinarily surprised if they haven’t, especially given that Edward Snowden generously revealed to the world that NSA was doing this more than a decade ago! And as a patriotic Brit, who has worked in IT for decades, I certainly like to think that UK GCHQ is right up there with America’s NSA and Israel’s NSO Group.
So we can safely that UK government has the spyware technology at its fingertips, should it wish to deploy it against anyone worldwide.
What Next
The UK Government has scheduled a test to take place in 5 days time, which they explain thus:
On Sunday 7 September 2025 at 3pm, the government will carry out a national test of the Emergency Alerts system. This means most mobile phones and tablets across the UK will receive a test message, accompanied by a loud siren-like sound and vibration that will last for about 10 seconds.
The message you receive will clearly state that this is a test and that no action is required on your part. The alert will come through even if your device is set to silent mode, which is an important feature of the system designed to ensure people receive warnings in genuine emergencies.
You can read all about it on the official government webpage here:
But in very simple terms the majority of phones in the country will make a noise and receive a message. Even if they’re on silent, and I suspect if they’re “turned off” too (I shall be testing a range of configurations).
Is it likely that UK deep-state will take this opportunity to load GCHQ spyware onto every smartphone that receives a message? No, I think it’s extremely unlikely, not least because they almost certainly wouldn’t have the capacity to handle all the data they then got back (that’s where Recall-style client side scanning comes in, more in another article…).
But it’s possible.
It’s also possible that the payload could be selective, targeting just selected mobile numbers, depending upon how the “alerts” software has been written. That’s the route I would personally take if designing the system, because few people will feel targeted if the whole country gets the message.
And that’s a chilling thought, given how much everybody relies on their smartphone and carries it most places they go.
Even if you’re not at risk as a person of interest (politician, journalist, top executive etc.) it’s worth being aware that both zero-click exploits, and spyware such as Pegasus and it’s ilk, exist. If there is interest in the comments, I’ll discuss possible ways to mitigate the risk in a future article.