Bulk Data Collection: Your Personal Data Is NOT Private
Just how much personal data are you leaking; what happens to it once harvested; who gets to exploit it; and what can you do to protect yourself, your family and your business?
You probably already know that pretty much every online platform or system you use - and everywhere you go - harvests huge amounts of data about you. But you may not fully realise exactly how much data, or what they really do with it.
I’m going to explain this, together with what you can do to help prevent or at least significantly minimise it, in a series of articles over the coming months.
You may not fully appreciate that, for example: Facebook tracks you all over the web; other websites update it with details about your activity every time you log in; WhatsApp tracks not just all your metadata and location, but routinely sends that back to Meta to be combined with your Facebook and Instagram activity to build a fuller profile of you, something is now further enhanced using AI; and of course it’s all shared with anybody who wants to pay for it, from marketers and private investigators, through to multiple government agencies (because it’s so much easier to just buy it on the open market than go through all the trouble of obtaining a warrant).
Let’s not be too down on Meta though, both Google does the same (and more!) as also does Microsoft, with firm plans for significantly more still as I recently explained in this article.
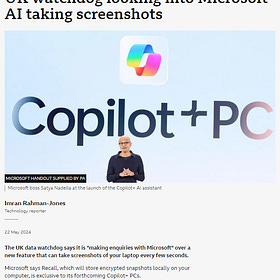
PRIVACY NIGHTMARE: Microsoft AI Recall will snapshot your "private" computer screen every few seconds
PRIVACY NIGHTMARE: Microsoft AI Recall will snapshot your "private" computer screen every few seconds. To quote BBC, and you know it’s bad if even the state’s mouthpiece is on about it: "The UK data watchdog says it is "making enquiries with Microsoft" over a new feature that can take screenshots of your laptop every few seconds.
And even that’s currently nothing compared with what your mobile phone and network operator is capable of, by virtue of the multiple processors inside your prized device (all of which you have paid for but only one of which the operating system can control).
And that’s a problem if you both use a computer or smartphone, and have even the slightest interest in retaining a shred of privacy in your life.
It may be that you’re resigned to life in a goldfish bowl and believe privacy is but a distant memory. I promise you it’s not though, and over the coming months I’m going to talk you through some of the simpler things that you can do to regain privacy in many aspects of your online life.
It may be that you believe “I don’t care about privacy because I’ve got nothing to hide.” I believe that’s both a personally dangerous and socially irresponsible attitude, for a number of reasons, not least:
Your data is forever but regimes change, as do our beliefs and opinions (both personal and society). Imagine that the regime changes to one that isn’t tolerant of what you are doing and saying now, even though currently perfectly innocent and legal. Do you really want a permanent record that can be used against you decades from now?
Maybe you will one day do something to upset the government, perhaps speak out against them because you are a person of principle, maybe even become a whistle-blower because of something you learn. And then maybe they’ll want to silence you. All they’ll need to do is pick a crime, then go back through the data they hold on you (because the bulk collection ensures they will hold everything) to find something however tenuous to connect you with that alleged crime, regardless of your innocence.
Even if you are fortunate enough to live in a regime where that doesn’t happen, and perhaps even never will, not everybody is. And as fellow humans we should care enough to want to help people less fortunate than ourselves. That means it’s important to normalise privacy, because if we all do it routinely even if we don’t feel the need for ourselves, then those who really need privacy won’t stick out when they use the tools and techniques through necessity. And that could help to save lives and secure freedom in places like North Korea, China and Afganistan.
You may have your own different reasons, of course, so feel free to share them in the comments below.
That’s the commercial harvesting threat, and that’s something we can all fairly easily avoid.
The implications of not doing so are huge though, because if social media networks in particular can steal your data they (and everybody they sell it to) can also know what you’re thinking, and by knowing that they can all feed you with information to encourage you to think what they want. It’s actually a pretty simple thing to manipulate people like that, as any number of psychologists have proven. Retaining some online privacy can help to prevent that too.
Consider too that this commercially available profile data is constantly being sucked up by massive government surveillance programs such as GCHQ’s TEMPORA in UK, and NSA’s PRISM in US. They store your personal data forever (NSA built something they called the Massive Data Repository (MDR) - later renamed to Mission Data Repository to help with PR - in Utah for specifically this purpose) and use ever-increasing processing power to create ever more detailed profiles of… well, everybody that ever accesses the internet, anywhere on the planet, and who they connect with.
To me, that’s a horrifying overreach of state and agency power.
But avoiding certain government security agencies, most especially those in USA and UK, is (whilst not impossible) a whole extra problem as Edward Snowden explains here, in this extract from his book Permanent Record (an enjoyable yet informative read that I recommend to you all) when talking about an individual (like You or me) quietly using their personal computer at home (URL is short for Uniform Resource Locator - i.e. the address you type into the browser’s address bar):
Towards the end of this series of articles we’ll look at some steps you can take to avoid even that extreme level of surveillance, but I’ll warn you now that it’s pretty hard and very far from convenient. Chances are that if you really need to do it you probably already know how anyway, and therefore what I’ll share at that time (the final few articles in the series) will be more academic than actionable for the majority of readers.
However, going about your daily life with substantially enhanced (but not total) privacy, and minimal inconvenience, is really pretty easy. And that’s mostly what I’ll be covering in this series.
I’ll try to publish one post a week, but don’t hold me to that. If you want to be sure not to miss them, then I recommend you subscribe now (it’s free).
And if you want your friends and colleagues to get the benefit too, then why not share this post with them and encourage them to subscribe too.
Finally, there are many detailed topics I plan to cover over the coming weeks and months, looking at how to use each with considerably greater privacy yet minimal if any loss of convenience, such as:
Email & Instant Messaging
Web Browsers & Web Searches
Streaming Videos
Mapping Software & Sat Navs
Social Media
Photo Sharing
Data & Cloud Storage
Video Conferencing
Single Sign On (SSO)
Domain Name Servers (DNS) & Virtual Private Networks (VPNs)
Internet of Things (IoT)
PC & Laptop Operating Systems
Financial Transactions
Decentralisation & Redundancy
Smartphones, SIMs, WiFi & Operating Systems
Cars: The Ultimate Surveillance Device?
Avoiding Government Surveillance
Etc.
Some of the above topics may require several articles each to cover in proper depth. So if there’s anything that especially concerns you, and that you want me to prioritise (whether listed above or not), please say in the comments. In the absence of any comments I’ll probably cover things in roughly the sequence above, as that’s approximately increasing technical complexity.





They (whoever they are) have been able to do this for decades and have been as you point out. They allowed so much illegal activity to happen with little or no consequence for the perpetrators.
And all the laws introduced to combat terror have been used against us.
However they have done nothing to slow down the spread of pornography and more and more children are being exposed to it.